Cryptographic hash functions are widely used in many aspects of information security such as digital signatures and data integrity checks. These functions take an electronic file, message or block of data and generate a short digital fingerprint of the content referred to as message digest or hash value.
What Is MD5?
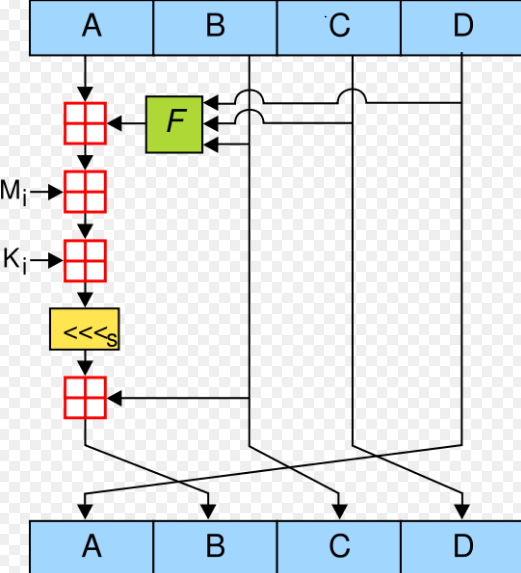
The message digest (MD5) is a ubiquitous hashing algorithm that was developed by Ron Rivest and is used in a variety of internet applications today. The MD5 hashing function is a one way cryptographic function that accepts a message of any length as input and returns as output a fixed-length digest value to be used for authenticating the original message. The MD5 hash function was originally designed for use as a secure cryptographic hash algorithm for Authenticating digital signatures.
The main purpose of MD5 as a cryptographic hash function is to verify that a file has been unaltered. MD5 does this by producing a checksum on both sets and then comparing the checksums on both sets to verify that they are the same. The MD5 message digest hashing algorithm processes data in 512-bit blocks, broken down into 16 words composed of 32 bits each. The output from MD5 is a 128-bit message digest value.
What is SHA-1?
Secure Hash Algorithm also referred to as SHA are a family of cryptographic functions designed to keep data secured. It works by transforming the data using a hash function.
SHA-1 is a cryptographic hash function which takes an input and produces a 160-bit hash value known as a message digest-typically rendered as a hexadecimal number, 40 digits long. It was designed by the United States National Institute of Standards and Technology (NIST). SHA is widely used in applications such as SSH, SSL, IPsec and S-MIME (Secure, Multi-purpose Mail Extension).
MD5 Vs. SHA-1 In Tabular Form
| BASIS OF COMPARISON | MD5 (Message Digest) | SHA-1 (Secure Hash Algorithm) |
| Description | The message digest (MD5) is a ubiquitous hashing algorithm that was developed by Ron Rivest and is used in a variety of internet applications today. It is a cryptographic hash algorithm that can be used to create a 128-bit string value from an arbitrary length string. Its main purpose is to verify that a file has been unaltered. | The secure Hash Algorith (SHA) is a family of cryptographic hash functions developed by the U.S. National Institute of Standards and Technology (NIST). SHA is widely used in applications such as SSH, SSL, IPsec and S-MIME (Secure, Multi-purpose Mail Extension). |
| Year of Publish | It was first published in the year 1992. | It was first published in the year 1995. |
| Complexity | MD5 is simple than SHA-1. | SHA-1 is more complex than MD5. |
| Speed | The speed of MD5 is fast when compared to that of SHA-1. | The speed of SHA-1 is relatively slow when compared to that of MD5. |
| Strength | MD5 is considered relatively less strong hash algorithm as it outputs a 128-bit message digest. | SHA-1 is considered relatively stronger hash algorithm as it outputs a 160-bits message digest. |
| Processing Power | MD5 relatively requires less processing power when compared to SHA-1. | SHA-1 relatively requires more processing power when compared to MD5. |
| Security | MD5 is less secure and therefore more vulnerable to cryptanalytic attacks. | SHA-1 is more secured and less likely to be vulnerable to cryptanalytic attacks. |
| Number of Iteration | A number of iteration is 64. | A number of Iteration is 80. |
| Number of Rounds | MD5 has 16 Rounds. | SHA-1 has 20 Rounds. |
| Assailant Operations | In MD5, if the assailant needs to seek out the 2 messages having identical message digest then assailant would need to perform 2^64 operations. | In SHA-1, the assailant would need to perform 2^80 operations, which is greater than MD5. |