What Is Symmetric Encryption?
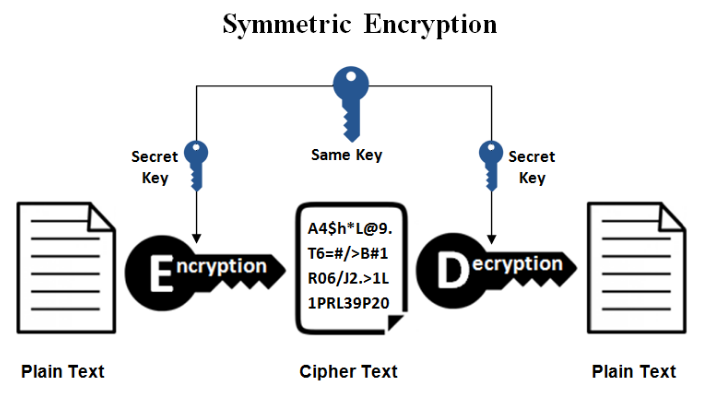
Symmetric encryption is a type of encryption whereby only one cryptographic key (secrete key) is used to both encrypt and decrypt electronic information. The entities communicating through symmetric encryption must exchange the key so that it can be used in the decryption process.
When a server and client are in need of a secure encrypted message, they send a query over the network to the other party which eventually sends back a copy of the certificate. The other party’s cryptographic public key can be extracted from the certificate. The common symmetric encryption algorithm include: RC4, AES, DES, 3DES, QUAD etc.
What Is Asymmetric Encryption?
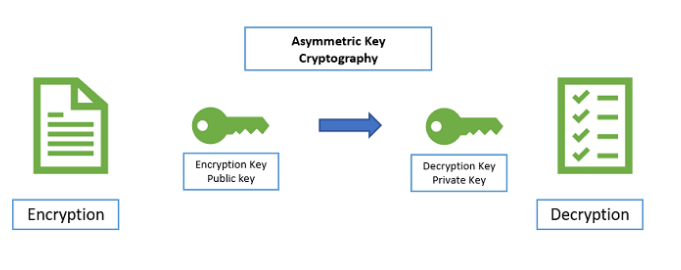
Asymmetric encryption also referred to as public key cryptography, is a type of encryption whereby two cryptographic keys are used to encrypt a plaintext. Secrete keys (one public and another private) are exchanged over the internet or a large network. It ensures that malicious persons do not misuse the keys.
The first public key is made freely available to anyone who might want to send you a message whereas the second private key is kept a secret so that you can only know. Here, a message that is encrypted using private key can only be decrypted using a public key while a message that is encrypted using a public key can only be decrypted using a private key.
The most common asymmetric key encryption algorithm includes PKCS, Elliptic curve techniques, RSA, ElGamal, RSA.
Also Read: Difference Between AES And DES Algorithms
Difference Between Symmetric And Asymmetric Encryption In Tabular Form
| BASIS OF COMPARISON | SYMMETRICAL | ASYMMETRICAL |
| Number of Cryptographic Keys | Symmetrical encryption always uses a single cryptographic key for encryption and decryption of the message. | Asymmetric encryption uses two cryptographic keys. The keys are referred to as public key and private key. Public key is used for encryption while private key is used for decryption. |
| Algorithm Used | RC4 AES DES 3DES QUAD | RSA Diffie-Hellman ECC El Gamal DSA |
| Complexity | Symmetric encryption is a simple technique compared to asymmetric encryption because only one key is used to undertake both encryption and decryption. | Asymmetric encryption is relatively complex in nature, because separate cryptographic keys are used to carry out both operations. |
| Speed Of Execution | Takes relatively more time due to simplistic nature, both operations can be executed quite quickly. | Takes relatively less time, because encryption and decryption is being carried out by two separate keys, the process of comparing those makes the speed of execution to be slow. |
| Age | Symmetric encryption is an old technique of encryption. | Asymmetric encryption is a relatively new technique of encryption. |
| Use | Symmetric encryption is generally used for exchanging a bulk of data. | Asymmetric encryption is used for exchanging secrete keys. |
| Existence | Symmetric encryption is an old technique. | Asymmetric encryption is a relatively new technique. |
| Mathematical Representation | Mathematically, symmetric encryption is represented as P=D (K, E(P)), where: K is encryption and decryption key. P=Plain text D=Decryption E (P)= encryption of plain text | Mathematically asymmetric encryption is represented as P=D(Kd, E (Ke,P)), where: Ke=encryption key Kd=decryption key D=decryption E(ke, P)= encryption of plain text using private key. |
Also Read: Difference Between Linear And Differential Cryptanalysis